adminMarch 27, 2023Uncategorized
In the digital age, personal identifiable information (PII) is generated, stored, and shared constantly across various platforms. PII refers to any information that can be used to identify an individual, such as name, address, social security number, email address, or phone number. With the increasing importance of data privacy and security, it has become crucial for businesses and organizations to identify and protect personal identifiable information.
Introduction to PII
PII can be found in various forms of data such as text, images, and videos. The rise of the internet and social media has made it easier for organizations to collect the personal information from customers and employees. However, the collection and processing of PII comes with a great responsibility to safeguard personal privacy and prevent the misuse of data.
PII Identification and Extraction Models
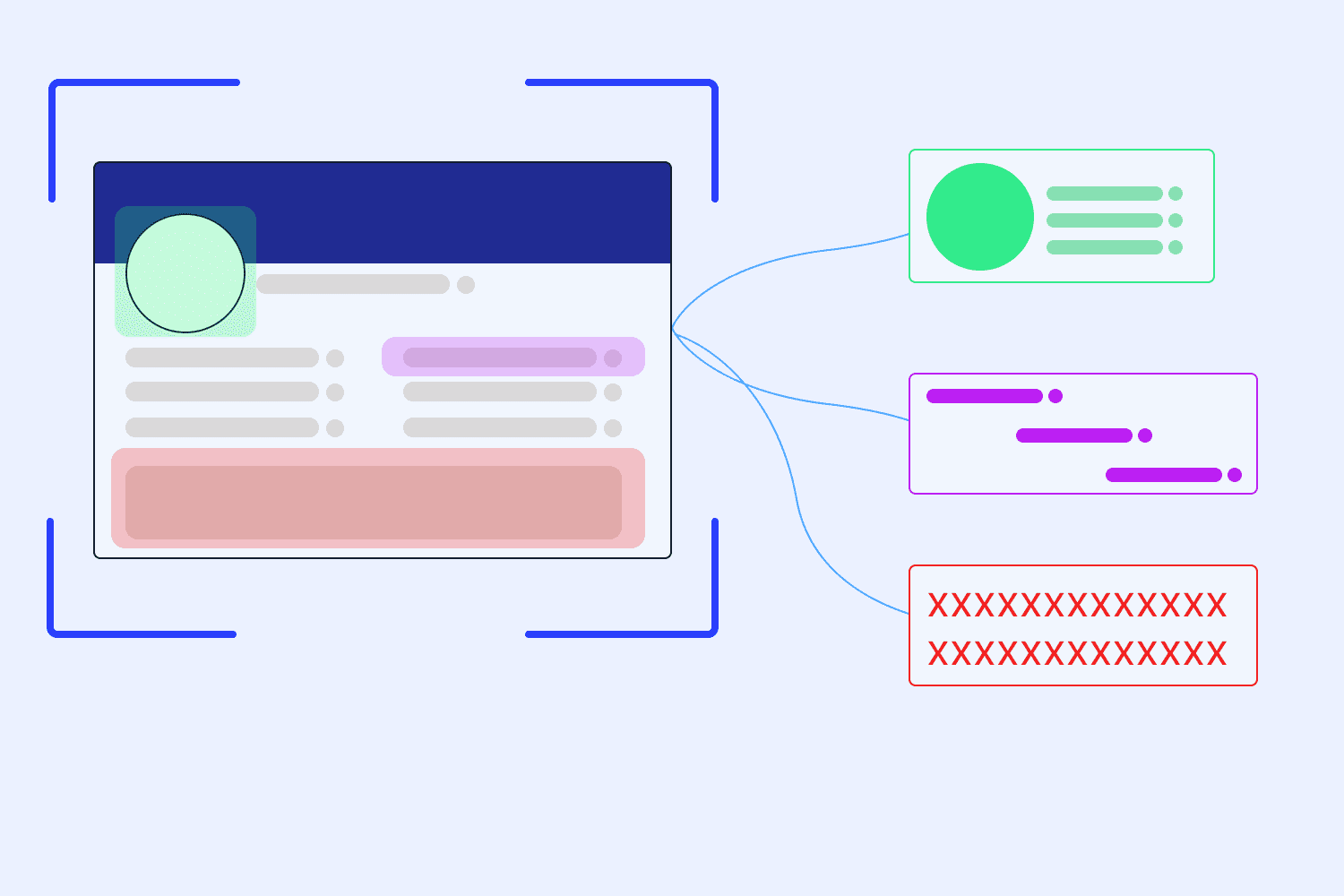
PII identification and extraction models use machine learning algorithms to identify and extract the information from various sources. These models can be trained on large datasets to learn how to identify and extract it from different types of data. The models use techniques such as natural language processing (NLP), computer vision, and deep learning to identify and extract personal identifiable information.
How PII Models Work
These models typically work in two phases: identification and extraction. During the identification phase, the model scans the data to identify potential instances of personal information. It uses pattern recognition and machine learning algorithms to identify PII based on predefined rules and patterns. Once identified the model moves to the extraction phase where it extracts the information from the data.
Techniques for PII Identification
There are several techniques that can be used. These include:
Natural Language Processing (NLP): This technique uses machine learning algorithms to analyze text data and identify instances of personal identifiable information such as names, addresses, and social security numbers.
Computer Vision: This technique uses deep learning algorithms to analyze images and identify instances of PII such as faces and license plates.
Entity Recognition: This technique uses machine learning algorithms to identify and classify entities such as names, locations, and dates.
Types of PIIs
PII can generally be classified into two categories: sensitive and non-sensitive.
Sensitive PII includes information that, if disclosed, could result in harm or damage to an individual, such as:
Financial information: Bank account details, credit card numbers, and other financial information.
Health information: Personal health records, medical diagnoses, and other related medical information.
Biometric information: Fingerprints, facial recognition data, and voice recordings.
Government-issued identification numbers: Social Security Number, Driver’s License Number, Passport Number, and Tax Identification Number.
Non-sensitive PII includes information that, on its own, is unlikely to cause harm or damage to an individual if disclosed, such as:
Name: Full name, first name, last name, maiden name, or any nicknames.
Address: Street address, email address, and IP address.
Employment Information: Job title, salary, and other employment-related details.
Educational Information: Student records, transcripts, and other educational records.
Role of No-Code Platforms in PII Identification
No-code platforms allow businesses and organizations to build personal identifiable information identification and extraction models without any prior knowledge of coding. These platforms provide a user-friendly interface that allows users to create custom models by simply dragging and dropping components. They also offer pre-built models that can be easily customized to meet specific business requirements. This makes it easy for organizations to create custom models and integrate them into their existing workflows.
Exploring the Use Cases of PII Identification and Extraction Models
Fraud Detection
Fraudulent activities such as identity theft, credit card fraud, and money laundering are common in today’s world. Personal identifiable information identification and extraction models can help financial institutions and other organizations detect such fraudulent activities by identifying and analyzing PII in their data.
Compliance
Various regulations such as GDPR, CCPA, and HIPAA require organizations to protect the privacy of their customers and employees by identifying and securing PII. PII identification and extraction models can help organizations comply with these regulations.
Customer Relationship Management (CRM)
CRM systems are used by businesses to manage their interactions with customers. PII identification and extraction models can help businesses automate the process of identifying and updating customer information in their CRM systems, thereby improving customer experience and satisfaction.
Healthcare
The healthcare industry generates a vast amount of patient data such as patient records, medical history, and insurance information. PII models can help healthcare providers identify and secure such information, ensuring compliance with regulations and protecting patient privacy.
Marketing
Marketing campaigns often rely on customer data such as name, email address, and phone number. The personal identifiable information identification and extraction models can help businesses extract and analyze customer data to create targeted marketing campaigns that are more effective and efficient.
Human Resources
HR departments of organizations are responsible for handling a large amount of employee data including some sensitive and non-sensitive personal details. The models can help HR departments automate the process of identifying and updating employee information, making it more efficient and accurate.
Insurance
The insurance industry relies heavily on customer data, such as personal and medical information. PII identification and extraction models can help insurers manage and secure customer data, reducing the risk of fraud and ensuring compliance with regulations.
Legal
Law firms and legal departments of organizations deal with sensitive information, such as social security numbers and addresses. The personal identifiable information models can help these entities automate the process of identifying and securing PII in their documents, reducing the risk of data breaches.
E-commerce
E-commerce platforms collect a large amount of customer data, including their name, email address, and shipping address. The models can help e-commerce platforms personalize customer experiences and streamline their checkout process by automatically extracting and updating customer information.
Education
Educational institutions store a significant amount of student data, including name, address, and social security number. These identification and extraction models can help educational institutions comply with regulations such as FERPA by automatically identifying and securing student data.
Government
Government agencies handle a vast amount of citizen data, such as social security numbers and tax information. PII identification and extraction models can help these agencies automate the process of identifying and securing citizen data, reducing the risk of data breaches and ensuring compliance with regulations.
Travel and Hospitality
Travel and hospitality companies collect a large amount of customer data, such as passport information and credit card details. PII identification and extraction models can help these companies manage and secure customer data, reducing the risk of fraud and ensuring compliance with regulations.
Data and Cyber Security
Personal identifiable information identification and extraction models are used in data and cyber security to detect and prevent data breaches by scanning large datasets for instances of sensitive information such as social security numbers, credit card numbers, and email addresses. By identifying potential vulnerabilities, organizations can take immediate action to secure the data and prevent a data breach.
PII identification and extraction models have a wide range of use cases across various industries. These models help organizations protect customer privacy, comply with regulations, and improve operational efficiency. The rise of no-code platforms has made it easier for businesses and organizations to build custom PII models without any prior knowledge of coding. Techniques such as NLP, computer vision, and entity recognition are used to identify and extract PII from various sources.
If you’re looking for a reliable PII identification and extraction solution, consider DeepLobe. Our state-of-the-art AI algorithms can help you identify and secure PII in your data. Contact us today to learn more!
